
Features
The following features are supported by Rootly:- Create users. Users in Okta assigned to the Rootly application in Okta will be automatically added as members of your organization in Rootly.
- Deactivate users. Users in Okta unassigned from the Rootly application in Okta will be automatically removed as members of your organization in Rootly.
- Import users. Users in Okta can be imported at once into Rootly.
- Update User Attributes. Users attributes updated in Okta will be updated in Rootly ( As firstname, lastname etc. )
Requirements
Make sure you setup SSO first. Rootly Tenant URL Endpoint:https://rootly.com/scim
Note: The endpoint will only resolve in the application after SSO setup has been completed first as noted above.
Okta
Enable SCIM provisioning functionality in Okta
- In Okta, navigate to Applications > Rootly
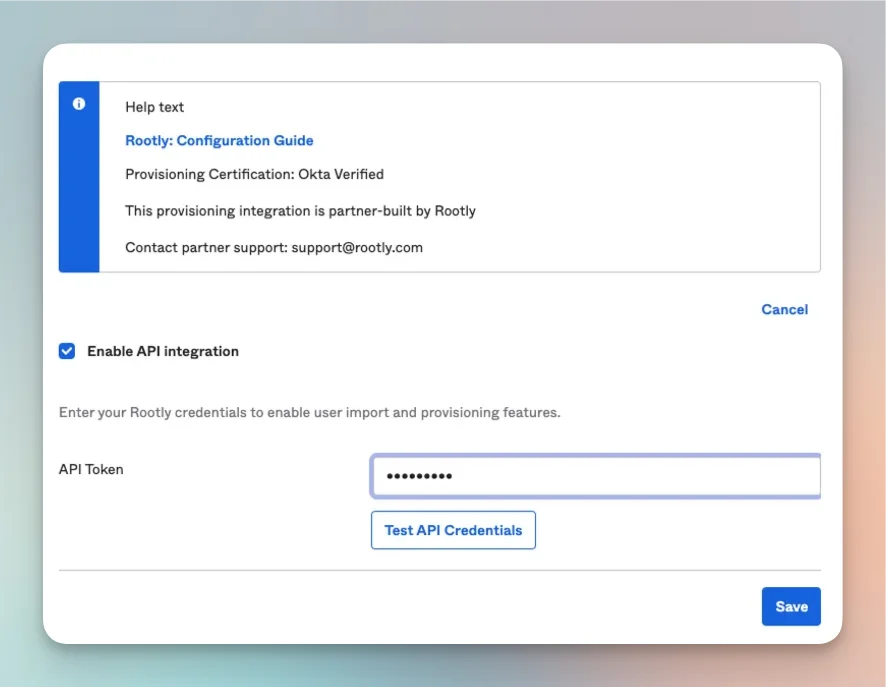
- Click on the Provisioning tab in the application. Under the Settings panel on the left-hand side, click the Integrations link. Then click Configure API Integration.
- Enter your API Token, you will find it under
Rootly > Integrations > SSOunderSCIM Token.
Enable “create users” and “Deactivate users” functionalities in Okta
- In Okta, navigate to Applications > Rootly
- Click on the Provisioning tab in the application. Under the Settings panel on the left-hand side, click the To App link.
- Click the Edit button at the top right. Check the Enable box next to Create users and Deactivate users to automatically provision/deprovision users in Rootly when they are assigned/unassigned to the Rootly app in Okta.
- Ensure the Default username used to create accounts in Okta is set to email. If it’s not, update this value by going to the Sign on tab of the Rootly application in Okta, click Edit, then set the Application username format to email under the Credentials settings section.
Provision Users via Push Groups
Create a Group- In Okta, navigate to Directory > Groups on the left navigation pane.
- Click on +Add Group.
- Give the Group a
nameand an optionaldescription. - Now you have a Group which you can add Users to and provision the entire Group to a Rootly Role.
- In Okta, navigate to Applications > Rootly
- Click on the Push Groups tab
- Click on +Push Groups button to find the Group you’d like to provision.
- Click on the Group you’d like to provision from the dropdown.
- Switch from Create Group to Link Group.
- Click Save.
- Navigate to your Rootly UI and select Integrations > SSO.
- Under the Role Assignment section, select which Rootly Role you’d like to assign to the Okta Group.
- You’re all set! Now, every time you add a user to that Okta Group, they will be provisioned to Rootly in the associated Rootly Role.
Microsoft Entra
Enabled SCIM provisioning functionality in Microsoft Entra
https://learn.microsoft.com/en-us/entra/identity/saas-apps/rootly-provisioning-tutorialGoogle Workspace
Enabled SCIM provisioning functionality in Google Workspace
Google Workspace only supports SCIM for a few apps for reasons we aren’t aware about. Fortunately enough we can take advantage of those to make it work with rootly.- Add a new Web and Mobile apps
- Then add Adobe App
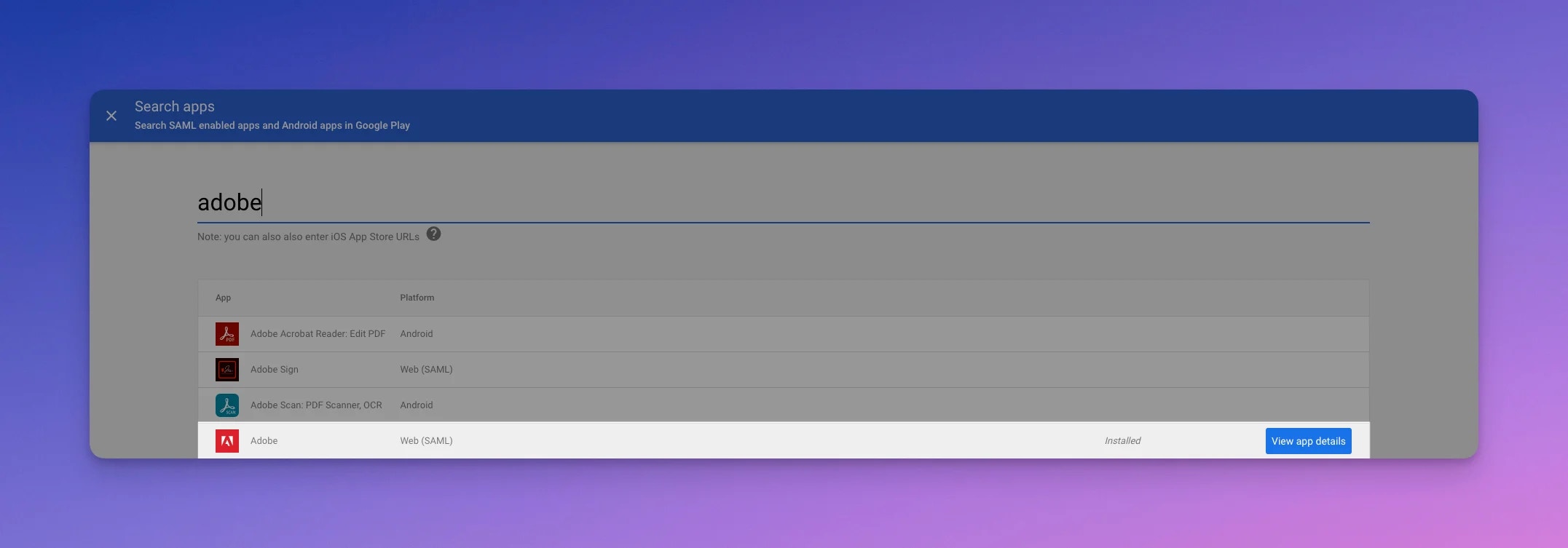
- In the next form fill out all fields with
- When it comes to configure auto-provisioning, copy the SCIM token you can find under Rootly > Integrations > SSO.
- Endpoint url to configure is https://rootly.com/scim
- Select a group of user you want to import into rootly or leave empty.
- Finally enabled the application. The sync should kick in shortly.
Keycloak
Enable SCIM provisioning functionality in Keycloak
-
Install the SCIM Extension
- Download the keycloak-scim JAR file from the releases
- Place it in
/opt/keycloak/providers/directory - Restart Keycloak to load the extension
-
Configure Event Listeners
- Navigate to Realm Settings > Events
- In the Event Listeners tab, add
scimto the list of listeners - Save the configuration
-
Create SCIM Federation Provider
- Navigate to User Federation
- Click Add provider and select SCIM
- Configure the following settings:
- UI display name:
Rootly - SCIM 2.0 endpoint:
https://rootly.com/scim - Endpoint content type:
application/scim+json - Auth mode:
BEARER - Auth password/token: Enter your SCIM token from
Rootly > Integrations > SSO
- UI display name:
-
Configure Username Format
- Set the environment variable
SCIM_EMAIL_AS_USERNAME=trueto ensure usernames are sent in email format - This is required for proper user matching in Rootly
- Set the environment variable
-
Enable Propagation Features
- Enable user propagation: On
- Enable group propagation: On (optional)
- Log SCIM requests and responses: On (for debugging)
- Import action:
CREATE_LOCAL
-
Optional Periodic Sync
- Periodic full sync: Enable if you want regular full user synchronization
- Periodic changed users sync: Enable for incremental synchronization
Testing the Configuration
- Create a test user in Keycloak
- Check Rootly to verify the user was automatically provisioned
- Review logs in Keycloak for any SCIM errors